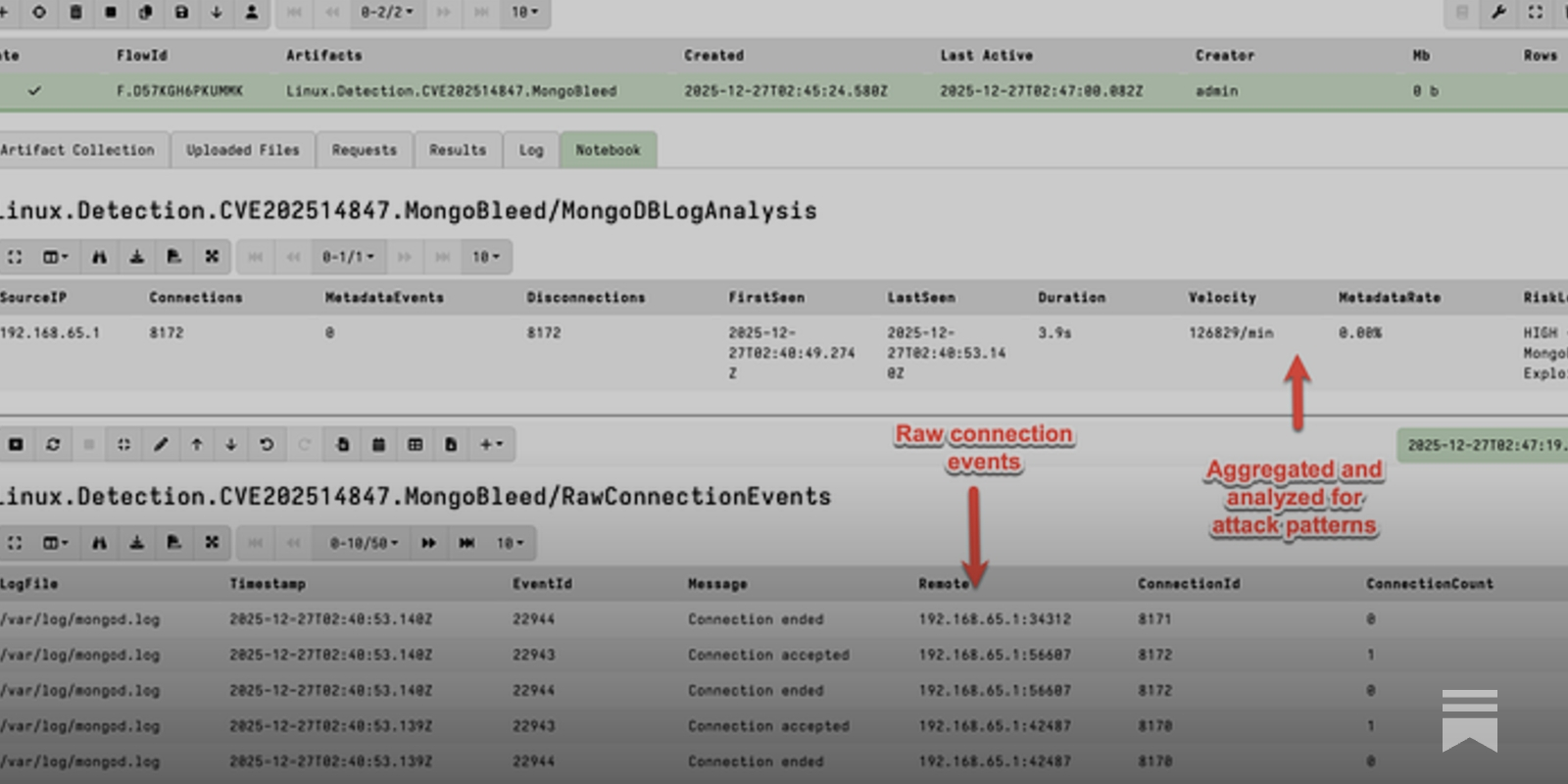
There’s a great blog on detecting MongoBleed exploitation via Velociraptor https://blog.ecapuano.com/p/hunting-mongobleed-cve-2025-14847
@GossiTheDog https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-14847 is a 404. I guess they assign a different CVE if one of their products based on MongoDB is affected?
@drewdaniels they shouldn’t do. Chances are they haven’t assessed it yet as the CVE dropped when Redmond are on holiday.
@GossiTheDog doesn't seem far to blame the PoC author? the exploit trigger was in the original diff as a unit test
@GossiTheDog no thanks, i use CouchDB
@GossiTheDog They were just doing Advent of Vulns.
@GossiTheDog I am having a bit of trouble getting worked up about this.
The bug went public six days before Christmas. This means, frankly, that the folks who get paid to be bad actors, of which there are rather many nowadays, have had six days to figure out how to exploit it. I'm sure several of them had already figured it out before the Eclipse dude dropped the exploit.
By making the urgency of patching this issue clear, he has arguably done a public service.
@jik nobody is telling you to get worked up 😅
@GossiTheDog every version going back a decade? Thank goodness we're ok then, ours is older 😎
@GossiTheDog who the fuck exposes a DB directly to the internet?
@Just_Patch_It about a quarter of a million orgs 😅
@GossiTheDog .oO( Surely nobody exposes mongodb towards the inter-| OMGWTFBBQsrsly?
I’m Omar from Gaza 🇵🇸
If you’re able to share my story and donate, it would mean a lot🙏🏻
The exploit is real and works, you can just run it and target specific offsets and/or keep running it until you get AWS secrets and such.
@GossiTheDog Wait, wait, wait, they decided the best time to drop an "oh, we fucked up about a decade ago, here's a demo of how to use that fuckup to show how bad it is" was on goddamn Christmas Day? *Seriously*?
That's... well, ho ho ho, have some coal in your stocking, I guess.
@GossiTheDog sounds like this exploit is webscale!
Episode 1 - Mongo DB Is Web Scale
YouTube
I did a quick write up: https://doublepulsar.com/merry-christmas-day-have-a-mongodb-security-incident-9537f54289eb
There’s a great blog on detecting MongoBleed exploitation via Velociraptor https://blog.ecapuano.com/p/hunting-mongobleed-cve-2025-14847
I set up a honeypot for MongoBleed on a legit MongoDB instance, yolo and all that.
@GossiTheDog it would be great to add note that you don’t have to upgrade right now.
Disabling zlib for network compression in enough to mitigate
Either:
a) Restart mongod/mongos with option --networkMessageCompressors=snappy,zstd
(omit zstd on 3.6 and 4.0)
b) Disable in mongod.conf and restart
net:
compression:
# (omit `zstd` on 3.6 and 4.0)
compressors: snappy,zstd
And then plan upgrade after holidays
@GossiTheDog Publishing an exploit on Christmas Day and not providing any info on how to detect exploitation is just the most stupid thing for a security vendor to do...
@edbo in fairness I think it's their personal account.. they've just put where they work everywhere so it's a bit odd looking optics wise 😅
@GossiTheDog Ah okay, still bad but makes a bit more senae
Does this count as yet another result of null terminated Strings being the most expensive architectural design choice that was ever made?
@GossiTheDog Hello, are you developer?
@GossiTheDog crappy timing but looks like it was a bit earlier than that. https://jira.mongodb.org/browse/SERVER-115508
@fencepost the vulnerability yes, not the exploit.
@GossiTheDog
At least they have the decency to wait till Christmas unlike log4j
@GossiTheDog
Me, unemployed right now: 😎
@GossiTheDog it really is the best time. If I had the power to discover and release stuff like this I would do it always during these times of the year. Such a power move 
@GossiTheDog oh for fuck's sake, what an asshole time to drop that one
@gsuberland @GossiTheDog the exploit was included as a unit test in the original patch, wiring that into a python script isn't slowing down attackers (but surely made the defenders take notice)
bonfire.mavnn.eu
News and community around mavnn.eu projects.